By Naoyuki Onoe, Associate Director, at Sony Research India
7th January 2022
Collaborative Background: Prior to launching Sony Research India, we searched for, and evaluated Indian institutes capable of the necessary research so that we could collaborate with them efficiently. After some evaluation, we discovered that IIIT Hyderabad possesses an established Biometrics lab in collaboration with the internationally well-known professor, Anil Jain from Michigan State University.

Tarang Chugh, Anil K.Jain, “Fingerprint Spoof Generalization”, International Conference on Biometrics (ICB) 2019, https://arxiv.org/pdf/1912.02710.pdf
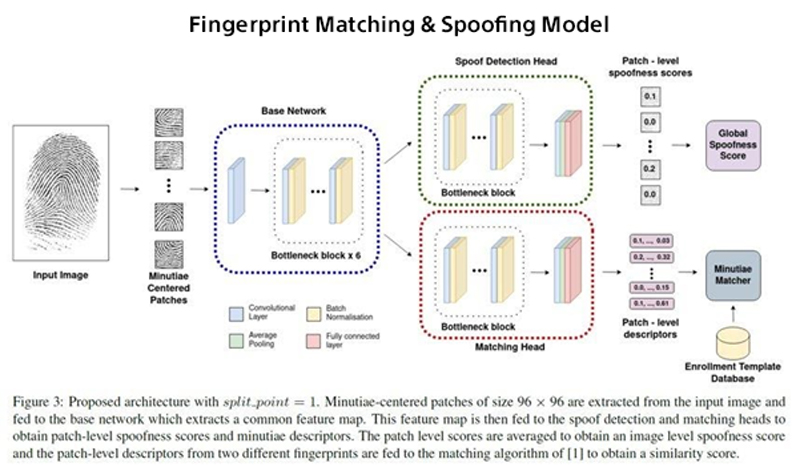
Additya Popli, Saraansh Tandon, Joshua J. Engelsma, Naoyuki Onoe, Atsushi Okubo, Anoop Namboodiri, “A Unified Model for Fingerprint Authentication and Presentation Attack Detection”, International Joint Conference on Biometrics (IJCB), 2021. https://arxiv.org/abs/2104.03255